After years of growth, innovation, and partnership, we’re excited to announce a major milestone in our journey: Key4ce is now ICT Shift.
This isn’t just a name change—it’s a reflection of who we’ve become and where we’re headed.
🤖 AI in IT Support: Hype or Help?
Is artificial intelligence transforming IT support—or just generating buzz? You’ve likely heard the promises: faster resolutions, smarter systems, and round-the-clock service. But how much of it is real, and how much is hype?
Let’s explore what AI truly brings to the table—and how companies can use it to their advantage.
Boost Communication & Cut Costs with Yeastar PBX
📞 Empowering Modern Communication: Why We Recommend Yeastar PBX (Business Phone Systems) As an MSP committed to...
📨 Mailcow: A Powerful, Privacy-Respecting Alternative to Microsoft Exchange On-Premise
As Microsoft Exchange On-Premise approaches its end-of-life in October 2025, organizations are faced with a critical decision: migrate to Microsoft’s cloud-based offerings, or look for a robust, self-hosted alternative.
For teams prioritizing control, privacy, and customization, one solution stands out—Mailcow.
Your Roadmap to the European Cloud: 10 Essential Steps
In today’s digital age, where data breaches and cyber threats are increasingly prevalent, establishing secure hosting solutions in the European cloud is more critical than ever, especially for businesses operating within Europe.
The European cloud is vital for understanding the European Union’s stringent regulations, particularly the General Data Protection Regulation (GDPR), which mandates that organizations manage their data with an emphasis on privacy and security.
Blocking .icu domains due to spam
Blocking .icu domains due to spam.. We aren't big fans of such drastic measures but more of a "finesse" kind of...
Understaffed by Corona? ICT Shift helps!
The corona virus and the impact of business It’s the topic of the day: The corona virus. it impacts the majority of...
New service: Extended support
Introducing: extended support. In popular demand we have added a new service to our primary IT Services. We...
New website released
The new website from 2020 has been released. We are extremely proud of our new website. With great focus on...
New website & new projects in 2016
Introduction It has been a while since my last update Key4ce hasn’t been sitting still in all those months, we are...
Dangers of Weak Endpoint Security Management
Endpoint security management has become an area of much concern in recent years for a number of reasons, on top which...
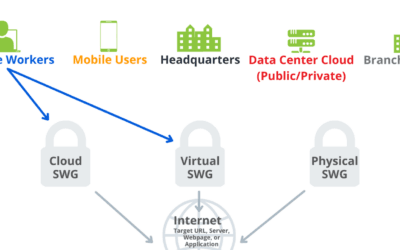
How SWG Appliances Are Coping With Sophisticated Threats
A secure web gateway (SWG), in its early rudimentary implementation, is a firewall built at the application layer that...
Your Organization May Need ITIL Service Support
If you are a big company that has the financial resources to maintain a full-blown IT department, you have probably...
DIY Routines to Keep Your Linux Server in Top Condition
Does your network run mainly on a Linux server? Just like any other network server, your Linux system needs to be...
Keep Servers Running With Infrastructure Tools
Infrastructure, in the context of IT servers, is simply organized server support. It refers to how the servers are...
IT Efficiency Through Converged Infrastructure
The idea of converged infrastructure revolves around forming a single optimized IT package by putting together several...
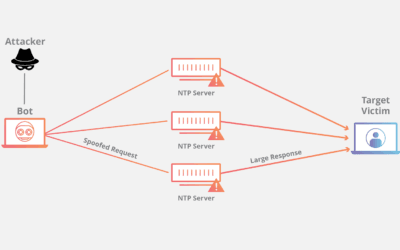
Systems Can Be Attacked Via NTP Flaws
At least three serious vulnerabilities in the Network Time Protocol (NTP) have been uncovered by security researchers...
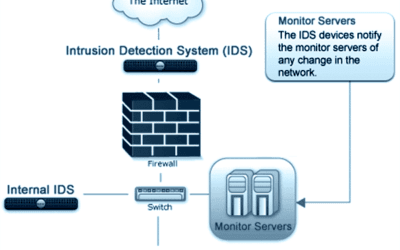
Who Needs an Intrusion Detection System?
Intrusion detection systems (also called ID systems and IDS) have been, and are still constantly being developed in...
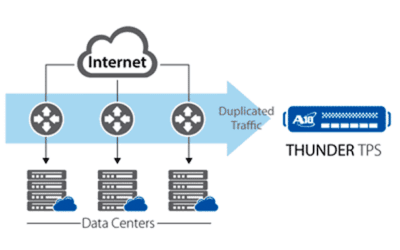
Here Comes the Anti-DDoS Appliance
"More creative and varied", this is how Brad Casemore describes the current nature of DDoS attacks in a recent article...
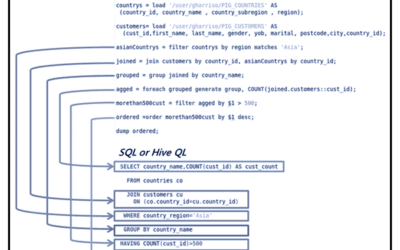
Big Data Analytics with Apache Hive
A few posts back, we encountered the evolving term big data which describes gigantic mass of data that big business...