by Marco Tiggelaar | Dec 22, 2014 | Cybersecurity & Compliance
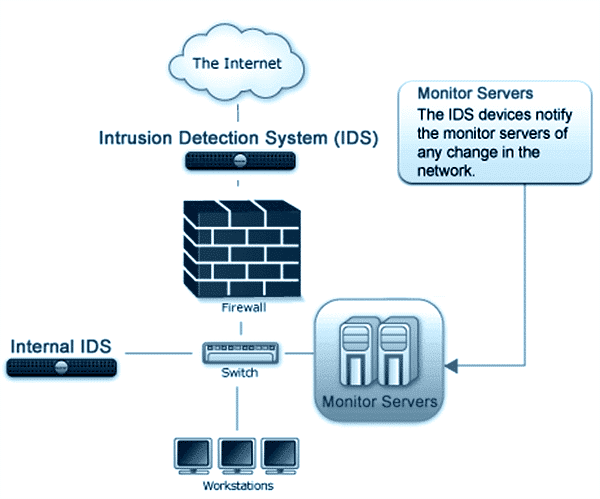
Intrusion detection systems (also called ID systems and IDS) have been, and are still constantly being developed in response to past and present attacks on many high-profile websites and networks, including those of Sony, eBay, Yahoo Mail, Google, Apple iCloud, UPS,...

by Marco Tiggelaar | Dec 3, 2014 | Cybersecurity & Compliance
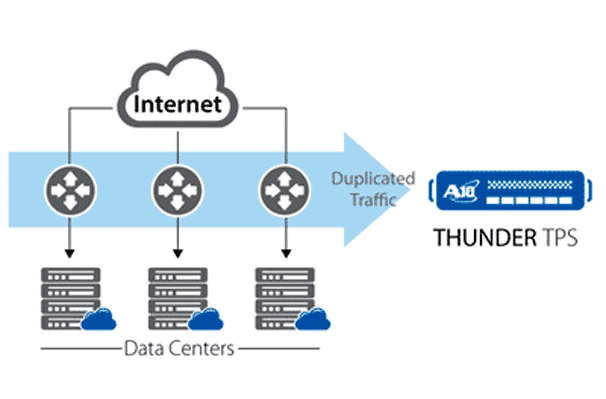
“More creative and varied”, this is how Brad Casemore describes the current nature of DDoS attacks in a recent article in the TechTarget website. Casemore, who is research director at International Data Corporation (IDC), said that the burden is on the...

by Marco Tiggelaar | Nov 24, 2014 | AI & Automation in IT Services
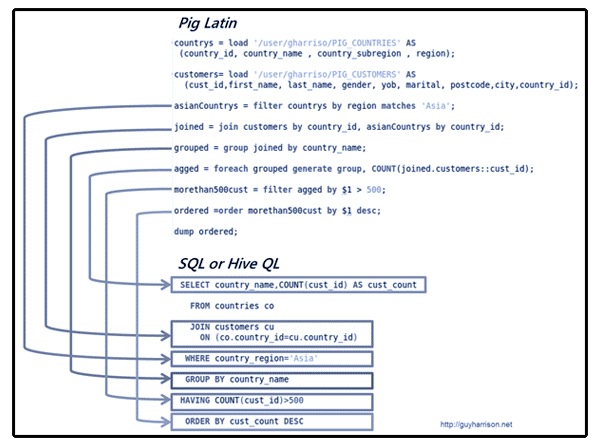
A few posts back, we encountered the evolving term big data which describes gigantic mass of data that big business enterprises are eyeing to mine for whatever value can be obtained from the data. Examples of big data may be found in the unimaginable collection of...

by Marco Tiggelaar | Nov 16, 2014 | Networking & Infrastructure
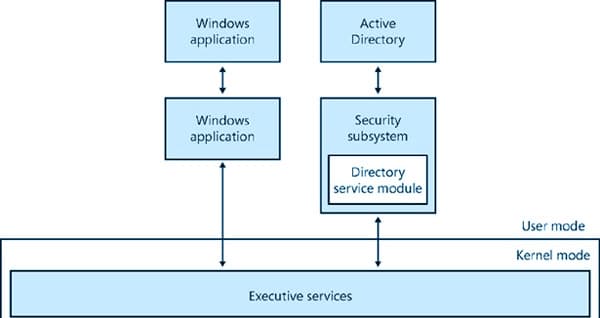
Yes. Cisco Systems, the dominant giant in the networking equipment industry, migrated to Active Directory. But before we look into the why or how of this story, let’s have a little background on Active Directory and on Cisco. Active Directory Active Directory (AD),...

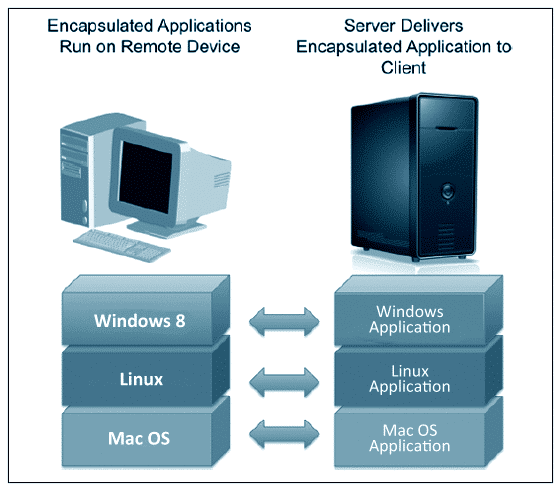
by Marco Tiggelaar | Nov 15, 2014 | AI & Automation in IT Services
Many layers of virtualization are currently at work, and one of them is application virtualization. Application virtualization is software technology that implements the encapsulation of an application so that it can be isolated from its host OS. The resulting...